Meizu M2 Note the test: Damn much smartphone for little money
5.5-inch display, full HD resolution, Octacore processor, two SIM cards, Android 5.1. All this and much more you get the Meizu M2 note for less than 200 euros. That sounds too good to be true, right?
Packed is the Meizu M2 note in a unibody enclosure made of plastic, which acts in the silver hue of the test device, such as metal. In the white, blue and pink models this effect is natural. With rounded edges, the 149-gram smartphone is comfortable to hold, for me are unusual keys on the left side of the housing, but which are easily accessible - regardless of which hand you hold the M2 note.
Outside top and inside not bad
The 5.5-inch IGZO display of Meizu M2 Note has a Full HD resolution of 1920 x 1080 pixels and convinced me with a sharp and crisp image. The screen convinced me beyond a high level of detail, large viewing angles, natural looking colors and can be self-sufficient in sunlight still clearly visible. Because remain as just the typical criticism of reflections, which have all smartphone displays, and the traces of my fingers on the screen, the more noticeable than with other devices and let me more often than usual to pick up the cleaning cloth.
The built-in touch M2 eight-core processor MT6753 of Media Center is clocked at 1.3 GHz and can draw on a Mali T720 graphics chip plus two gigabytes of memory. Together they create in Antutu benchmark 31000-32000 points and are thus at the level of Qualcomm Snapdragon processor 615 middle-class, the infected, for example, in the trunk or Elephone ZTE Star 1 or UMI IRON. Regardless of these number games the user interface runs smoothly. The load times - even of larger apps - are fully suitable for everyday use. Even graphically demanding games like Asphalt 8, can be to gamble on the Meizu problems - but only in the second-best level of detail.
The touch of the M2 battery has 3100 mAh over a larger capacity than most top smartphones and comes together with the middle-class hardware problems over the day. I've done as a rule 36 hours. Anyone who handles particularly economical with the energy, the smartphone must charge until the evening of the second day again. Due to the unibody housing the battery does not replace, but the choice of 16 or 32 gigabytes of internal memory you can expand with a microSD card. Hands you the space from, you can instead also a second nano-Insert SIM into the card slot of your smartphone.
Average Camera
Meizu builds in the M2 touch a camera of OUKITEL whose CMOS sensor captures images at 13 megapixels. The quality of the recordings remains significantly behind the K4000 Pro. In daylight the smartphone camera then delivers photos with a good but not outstanding detail. The colors appear natural, with strong contrasts the camera copes well. In poorer lighting make fast artifacts and a coarse grain noticeable. Overall, the image quality in my eyes is slightly above average.
The 5-megapixel camera on the front provides innately inferior image quality, which is manifested by fewer details and more blur. In addition, they worked Selfies automatically. Not so nice.
Android without Google - or rather with?
The M2 grade is suitable for everyone who wants to use Android without Google's services. Because the pre-installed OS Flyme 4.5 of Meizu functions without any Google Apps. However, you must then also a little more time to invest in the establishment and dispense may in the usual app one way or another. Knowledge of the Chinese language would be helpful, which I can not say whether Mandarin or Cantonese would be more appropriate. But do not worry, you do not have on the Play Store and the familiar Android world without. The App Center of Flyme there is a Google Installer, which installs the Google Play Store and the settings on the M2 note and so lays the foundation for add all other Google services subsequently and can uninstall the preinstalled Chinese applications.
Apart from the additional time in setting up, me the user interface of OS Flyme like it very much. When updating to 4.5.2 Flyme ranged the English word scraps, so I understand what the alert want to tell me.
An additional features compared to the stock Android noteworthy I find the way to protect individual apps with a PIN code or password against unauthorized access, the different gestures to operate, which works even on the off-screen, as well as the pre-installed Sicherheitsapp. I can not make any statement about the quality of your virus scanner, but I am pleased that it scans the smartphone after the unnecessary files and deletes and cleans up the memory, indicates to me large files, I can manage traffic and gives me an overview of the app which has permission and this may also adjust individually.
Unusually for me than Android users of the home button. Like the iPhone it is the only key to the operation. Not even appear on the display a rewind or multitasking button. Instead, your taps the Home button in order to take a step back or pushes him to open the Applications Launcher. Do you take the key for two seconds to open a voice control, which, however, still does not understand German. A multitask Ting index is available at Flyme not - me personally but not absent.
Mid-range smartphone for entry-level price
What some users should discourage the additional effort to uninstall the pre-installed apps and make it perfectly usable for themselves. But one must clearly invest more time than foreseen by the German market Android devices without "China Branding".
The expense precludes the very good price-performance ratio. Various shops offer the Meizu M2 note for around 190 euros in Germany. The online store Pandawill who has provided us with the test device is available, calls for the tested version with 16 gigabytes of storage $ 160 - the equivalent of around 145 euros are the - no extra shipping costs for shipment from Hong Kong.
Elephone P6000 Pro: The second smartphone with Android 5.0 preinstalled Lollipop
We know that some things are different in China already sufficiently so that it not too surprising that there is now the featured Elephone P6000 Pro another budget smartphone from the Middle Kingdom. While shopping for a nearly 139.99 dollars expensive smartphone looks pretty neat, it is the operating system which draws attention to itself.
At Google I / O 2014 Android was 5.0 Lollipop - then known as Android still L and all kinds of guesses at the official nickname - officially presented and approved in the form of the AOSP source code on 3 November. In mid-November were finally with the Letv Le 1 Pro and the ZTE Star 1, the first two devices with the new and already preinstalled OS presented what already more than a month ago, now. Now enters the Elephone P6000 Pro the market and this little smartphone is something really special in many respects the same.
Elephone P6000 Pro with good technique
For what it leaves a little protrude from the mass of smartphones in China is the fact that on the Elephone P6000 Pro the first non-Nexus smartphone that comes with Android 5.0 Lollipop. As well, however, the operating system has been optimized to the hardware, is a totally different question. Here, the Elephone P6000 Pro provides no times as bad hardware.
5 inch IPS display with 1280 x 720 pixel resolution
MediaTek MT6732 quad-core 1.5 GHz and 64-bit
2 GB RAM
16 GB of internal memory (expandable via microSD)
Wi-Fi b / g / n, Bluetooth 4.0, GPS, LTE, dual SIM
13 megapixel camera, 2 megapixel front camera
165 grams
144.5 x 71.6 x 8.9 mm
2,700 mAh battery
For a mid-range smartphone not too bad equipment that can be had for just nearly 170 US dollars. And this is where the second feature of the Elephone P6000 Pro comes into play: The Android 5.0 smartphone Lollipop is available on the company's website and internationally for sale. Alone the price is for a 64-bit smartphone with LTE already an attractive offer, but the Android 5.0 Lollipop is already installed, make the Elephone P6000 Pro same again a bit far more interesting. Rumour has it to be sold as early as December 27 in China.
Or how do you think? A good catch or rather wait for other models?
Update
Well, since we were probably a little too fast. How Elephone now notifies and on the product side makes it clear once again that Elephone P6000 Pro does not come with Android 5.0 Lollipop, but with Android 4.4.4 KitKat. The latest version of Google's operating system is to be submitted only via OTA update. The corresponding statement the company has now added on the product page.
The Cubot S550 - Cheap Tablet from China
The Cubot S550 is a new smartphone of the popular China phone manufacturer Cubot. The smartphone is 5.5 inches tall, and has a solid middle-class Ausstatttung. Also on board is a quad core processor with 4 * 1.3 Ghz. This is supported by 2GB of RAM and a Mali-T720. In addition, the smartphone has a 13 megapixel camera and a Fingeradrucksensor on the back.

power
In Cubot S550 of Mediatek QuadCore CPU comes with 64-bit architecture MT6735 used. The four cores of the processor clocking 1.3GHz respectively and are supported by 2GB of RAM. This chipset is typical for smartphones of the lower middle class and is aimed at users, in particular use the basic function of the phone. As a rule, a fast system speed is ensured. When opening and closing apps, there are only minor delays. Even surfing the Internet is possible without any problems. Who wants to play games more often on his smartphone, should indeed access to another mobile phone, for graphically undemanding games the Cubot S550 is however quite prepared.
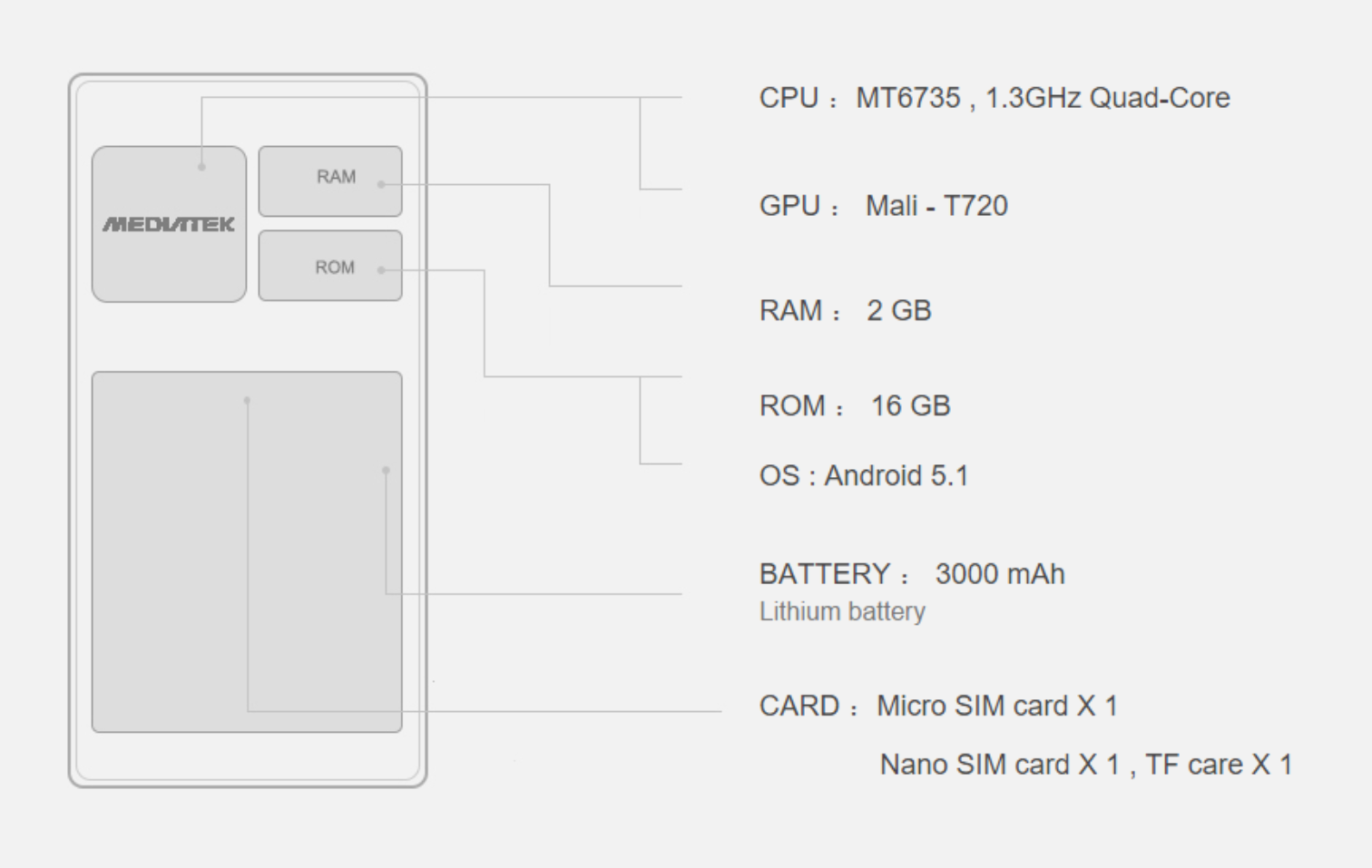
With 2 GB of memory, the phone also has basic multitasking capabilities, allowing multiple apps can be used simultaneously without any problems. The internal memory is 16 GB and can be expanded with a micro SD card. To extend the memory, however, you have to do without the use of a second SIM card.
Android
The Cubot S550 is supplied with a current Android 5.1 system. On the smartphone of Google Play Goals is of course preinstalled and all apps can be used. As we are used to it from Cubot, the smartphone also has a largely untouched Android system.
Display
The S550 has a 5.5 Cubot inch HD display with a resolution of 1280 × 720 pixels. This results in a pixel density of 267 PPI. The mobile phone is slightly below the retina value. If you look exactly like so see individual pixels. Nevertheless, the HD display brings a good and sharp image. Thanks to IPS technology, the Cubot S550 has a good viewing angle stability and a deep black.
camera
The Cubot S550 has a 13 megapixel camera on the back. This is supported by a dual LED flash and has an Aperture of f / 2.0. On the front there is a 8 megapixel camera for video telephony and Selfies.
Network and telephony
Cubot S550 titelDas Cubot S550 has all the necessary in Germany LTE frequencies (800/1800/2600). Who has a corresponding LTE contract, can be used with your smartphone high-speed Internet. Who does not have LTE contract, needs also to worry: on the Cubot S550 all necessary for Germany 2G and 3G frequencies are available. The simcards are used on a hybrid slot sideways into the phone. The Cubot S550 is a dual SIM smartphone. This means that two SIM cards can be used simultaneously.
Connectivity
The Cubot S550 has various sensors: A direction sensor, a proximity sensor, a compass, a speed sensor and a light sensor are available. Also supports OTG Smartphone, GPS, Wifi and Bluetooth 4.0.
battery pack
The smartphone has a 3000 mAh battery strong. For a 5.5-inch smartphone, it is above the average. In combination with the fuel-efficient processor that Cubot phone should reach very good battery life. For people who take their smartphone rather rarely at hand, should be guaranteed two days usage. Even heavy users come to the Cubot S550 probably throughout the day.
Fingerprint Sensor
Cubot S550 FingerabdruckDas Cubot S550 has a fingerprint sensor, which is mounted on the back of the smartphone. With this, the mobile phone can be unlocked quickly and safely.
Our assessment
The hardware of the Cubot S550 provides a solid basic equipment, with a pleasantly quick use of the basic functions (apps, multimedia, Internet) should be possible. The images Judging by the Cubot S550 also makes optically something thus. Still, the smart phone is not on the market, but we will strive as soon as possible to a tester.
iPhone 6 Wandering Actions and Optimization
Executive and Suggestions Summary
IOS 8 gadgets try to wander when their associated BSSID indication drops below –70 dBm RSSI. The IOS 8 gadgets then examine out all programs (without 802.11k) or the focus on programs conveyed by their present AP (with 802.11k enabled), and wander to another AP if its indication is 8 dB better (IOS 8 system in effective communication) or 12 dB better (IOS 8 system in idle) than the present AP.
Roaming activities are crucial for VoWifi and business-critical real-time company programs. Effective roaming time is 50 ms. Without 802.11k allowed, dual-band SSIDs, and conventional AP solidity, the overall loss of relationship for an IOS 8 system can achieve 5 a few moments for each wander. With 802.11k allowed, greater AP solidity (AP every 2500 sqft or every 240 sqm), and system developed with 5 GHz, the roaming activities can achieve sub-second.
When developing wi-fi systems for real-time program activities, plan for 5 Megabyte per second per customer and 12 – 14 clients per AP. Make 5 GHz and 802.11k as part of your style requirements for cell mobile phones.
Context
Mid Nov 2014, The apple company assistance released a referrals papers describing how IOS8-based gadgets wander (http://support.apple.com/en-us/HT6463). This website access is based on this referrals papers, but with included lab + actual system dimensions (to differentiate excellent intents from realistic actions in actual world).
The roaming behavior is identical for Refurbished iphone 6, Refurbished iphone 6 plus, Refurbished iphone 5c, Refurbished iphone 5s, iPad Air, and iPad small with retina. The searching behavior also is based on the chipset used in the product. You will see common behavior factors identified by the OS, but also little clock modifications between designs identified by the chipset and its car owner. For example, does the product sensor / probe once or repeatedly per “probe burst”, how many milliseconds between the sensor / probe demands in a given rush, and so on. This papers concentrates on the normal behavior, but the electronic timers proven were calculated on Refurbished iphone 6, using a Broadcom BCM4339 chipset. The behaviour was examined on IOS 8.1.
How Often Does My Refurbished iphone 6 Scan?
When you are NOT associated to any SSID, and your display is off (for example, your cellphone is in your pocket), your cellphone will look into the atmosphere at frequent durations for SSID by delivering sensor / probe demands. The cellphone will examine out more often if you progress (that is, the indication from APs differ, see the When Does My iPhone Roam?, on website 3 area, as the behavior is similar). So let us believe the most severe situation, you are not shifting.
If your mobile details are not available and Place (Settings > Comfort > Place Services) is impaired, your cellphone on the other hand uses its actual MAC deal with and a regionally applied deal with. The idea is to momentarily cover up your actual MAC deal with for privacy reasons. In that place, the product delivers instant sensor / probe demands with the actual MAC deal with. The cellphone then remains quiet for a “random interval” (in the order of 140 seconds), before delivering between one and six probes with a regionally applied deal with, at 135 or 270 second period. The cellphone then remains quiet for another exclusive period (up to 10 minutes) before going returning to the actual MAC deal with and restoring the pattern. The cellphone options a new regionally applied deal with when changing between actual and regionally applied details.
An example of the behavior is proven in the following determine. The horizontally axis symbolizes the catch quantity of second (capture was taken over 8.5 hours, or 30 K seconds). The straight axis symbolizes the period between two successive sensor / probe demands. Nowhere principles are probes using the actual MAC deal with, and the red principles signify probes using a regionally applied deal with. For example, at 5000 second, 322 a few moments after the last sensor / probe demand using a regionally applied deal with, the product delivers a sensor / probe demand using the actual MAC deal with (blue dot at [5000,322]). After 20 milliseconds, the product delivers a second sensor / probe using the actual MAC deal with (point that seems to be at [5000,0], but is in fact at [5000.02, 322.02]). The cellphone then remains quiet for 135 a few moments before delivering a sensor / probe using a regionally applied deal with. The cellphone then delivers two more probes at 135 a few moments period, then two more probes at 270 a few moments period, and remains quiet for 204 a few moments before delivering a sensor / probe with the actual MAC deal with.
Notice that some catch and accident relics incorrectly display regionally applied deal with probes at large durations (beyond 270 seconds).
The regionally applied deal with is not used any longer as soon as you affiliate to a WLAN or if mobile details or Place are allowed. In these instances, the product will examine out your focus on SSID at 90 a few moments period (or the transmitted, if you are not associated), in a form of "maintenance mode". This supposes that the AP indication is constant and display is off (for example, your cellphone is in your wallet while you sit at the shopping center food court).
If you start using your cellphone (actively using the Wi-Fi connection), the product prevents searching, as it uses the AP shining example information details supports to look at the AP indication stage. The Refurbished iphone 6 (with the BCM chipset) still delivers a 'reflex probe" to your SSID every 30 moments. Other designs may have a a little bit different behavior. The IOS 8 element does not ask the product to sensor / probe.
When Does My iPhone Roam?
The Refurbished iphone 6 does not use the accelerometer to find out that you are shifting, and the AP indication needs to examined. It is based completely on the AP alerts to the product to find out if roaming is needed. The limit is –70 dBm. This implies that as lengthy as the AP indication (beacons details frames) is more powerful than –70 dBm, the product does not try to examine on out more definitely or wander.
As soon as the AP RSSI, as read by the product car owner, drops below –70 dBm for more than one second, the product selects that the present AP is useless and selects to wander, which activates checking.
At this aspect, several opportunities exist:
1 You designed your system to use 802.11k. This selection allows the AP to deliver a record of nearby APs to the product upon demand. In that place, the product assessments the best six APs, and tests their programs.
For example, your present AP is on route 36, and the revealed APs are on programs 40 (–68 dBm), 44 (–76 dBm), 48 (–72 dBm), 52 (–78 dBm), 56 (–59 dBm), 60 (–75 dBm), 149 (–74 dBm), 153 (–70 dBm), 157 (–71 dBm) and 161 (–63 dBm). The cellphone discovers that the best six APs are on programs 40, 48, 56, 153, 157 and 161, and delivers sensor / probe demands for the focus on SSID to these programs.
Be cautious, these alerts are revealed as observed by the AP, not as observed by the product. Also, the Refurbished iphone 6 demands the record of next door neighbor APs when coming into the mobile (right after association), not when roaming. So, the record may not be the newest (see the Effect on Your Design, on website 5 area about style recommendations).
2 You did NOT set up your system to use 802.11k. In these instances, the product tests all programs (this can be 11 or 13 programs in 2.4 GHz, and up to 13 programs in 5 GHz). The cellphone tests UNII1, UNII2, and UNII3. The cellphone can also examine UNII2-e, but only passively. The cellphone tests UNII2-e every 6 checking pattern. This is because this group remains safe and secure by 802.11h, and the product has to pay attention passively (no effective scanning) until it listens to an AP. So, discovering APs in UNII2-e can take more than a moment. Even checking the other programs needs time. Anticipate several a few moments for this technique. It requires of course longer if the product is definitely interacting on the AP present route, because the product has to find an period where no details are predicted to leap to the focus on route to examine on out. If the product is not interacting, checking is quicker.
In both situations 1 and 2, the product tests and looks for a better AP to leap to. Realize that the product does not try to keep in the same group, it can leap from 2.4 GHz to 5 GHz or the other way around, even on the same AP. The roaming requirements blogs about the BSSIDs that were recognized (that is, the initial MAC deal with of each stereo providing the focus on SSID name) to the present AP BSSID indication stage. Then, the roaming decision is based on if you are definitely using the Wi-Fi system (traffic to and from the phone) or not (phone is nonproductive or display off, in your pocket). If you are not using the Wi-Fi relationship, the product will only leap if another AP provides a indication really better than the present one. It needs to be at least 12 dB better. If the new AP indication is at least that much better, your cellphone roams. If no recognized stereo has a indication 12 dB or more better than your present AP, the product remains on the present AP, but keeps checking at 90 second durations until it discovers a better BSSID (12 dB better than the present AP BSSID) or until the present AP indication returns above -70 dBm.
If you are using the Wi-Fi relationship, things are more pushing. The cellphone identified that –70 dBm was a inadequate indication and is ready to leap previously. It will wander to a new stereo if the BSSID is 8 dB or more better than the present AP. For example, if your AP stereo indication decreased is to –72 dBm, and the product finds BSSIDs for the same SSID name at - 61 dBm, -63 dBm and -69 dBm. In situation if you are definitely using the Wi-Fi, the product allows to wander to the BSSID at –61 dBm and to the BSSID at –63 dBm. Because, they are 8 dB or more better than the present AP (11 dB and 9 dB better respectively). The cellphone does not wander to the BSSID at –69 dBm, because it is only 3 dB better than the present AP. Having two options, the product selects the BSSID with best indication, and roams to the BSSID at –61 dBm.
If no BSSID is recognized at 8 dB better than the present AP, the product remains on the present AP, but keeps checking at 90 a few moments durations (one sensor / probe demand followed by a second sensor / probe demand 10 nanosecond later) until it discovers a better BSSID (12 dB better than the present AP BSSID) or until the present AP indication returns above –70 dBm. The following chart reveals this behavior with an Refurbished iphone 6 on a dynamic Wi-Fi relationship, managed far from its AP (signal at around –75 dBm) without different AP to leap to.
Enabling 802.11k
Roaming with an IOS 8 system is more effective if you apply 802.11k than if you do not apply 802.11k. This is because the checking time is smaller with 802.11k. In the following example, an iPhone was transferred to and fro between two APs. The APs were far enough from each other that the iPhone would combination the –70 dBm advantage while shifting from one AP to the other.
Both APs had the same SSID allowed, available on both 2.4 GHz and 5 GHz. Energy was set to 3 on 5 GHz, and 5 on 2.4 GHz, making the 2.4 GHz mobile about only 30% greater than the 5 GHz mobile.
Without 802.11k allowed, roaming periods are lengthy. Moving to and fro 3 periods between APs display several roams (more than the predicted six roams). This is because the iPhone leaps from 5 GHz to 2.4 Ghz, then returning to 5 when getting near the next AP. The common roaming time (time between the last bundle recognized to or from the product on one AP and the first bundle to or from the product on the next AP) was near to 5 a few moments. This implies, generally, your cellphone drops its relationship (no communication) for near to 5 a few moments when roaming.
With 802.11k allowed, the frequent roaming time is down to about 1 second. These activities can be improved to achieve sub-second with counsel below.
Configuring the Band
Enabling 802.11k improves roaming efficiency, but does NOT restrict the iPhone to one group. Automatically, 802.11k provides details about nearby APs only on the consumer group. In other terms, if your iPhone is associated to the BSSID on 5 GHz, the AP will provide details about nearby APs in the 5 GHz group, not in the 2.4 GHz group. But this does not mean that the iPhone will remain on the 5 GHz group.
When an SSID is available on both groups at "good indication level" (more than -70 dBm RSSI), the iPhone will affiliate in concern to the 5 GHz stereo. However, at equivalent AP power, at any reason for the mobile, the 2.4 GHz indication is generally about 7 dB more than the 5 GHz indication. This distinction is due to common technical variations in aerial features for each group, and similarly impacts most clients. It is not due to the doorway.
The outcome is that when the iPhone is associated to the 5 GHz stereo, it goes away and gets to the –70 dBm border for 5 GHz, the indication from the same AP in 2.4 GHz is generally recognized as –63 dBm. This is a theoretical distinction. In actual area deployments, the statistic precision is commonly 4 dB. This implies, if the AP indication is –63 dBm, the consumer will review a indication that can be anything between –67 dBm and –59 dBm, based upon on the consumer actual place in space and RF modifications.
When it affiliates to the doorway, at frequent durations during the relationship, the product demands a record of nearby APs from the AP, using 802.11k action supports. As the product is associated to 5 GHz, the AP only provides next door neighbor BSSIDs in 5 GHz. When the iPhone gets to the –70 dBm border on 5 GHz, it uses the 802.11k next door neighbor record to only look at 5 GHz programs described in the record. However, the iPhone also tests 2.4 GHz, without a record to work from. Two situations can occur:
1 The cellphone discovers a nearby BSSID on 5 GHz at excellent indication stage (8 dB better than the first AP if the product is definitely communicating), and possibly a nearby AP on 2.4 GHz at excellent indication stage. In that place, the product roams to the BSSID on 5 GHz (the cellphone likes 5 GHz when provided the choice).
2 The cellphone discovers a nearby BSSID on 5 GHz, but its indication is not 8 dB better than the present AP (because the overlap between tissues is little, or because the product reviews a lower indication because of recognition imprecision). The cellphone also discovers a nearby BSSID on 2.4 GHz. Because of the mixture of "signal generally 7 dB greater in 2.4 GHz", and "4 dB indication statistic imprecision", the product is likely to see the 2.4 GHz BSSID as a better applicant than the 5 GHz BSSID, inducing the product to wander from 5 GHz to 2.4 GHz. When shifting nearer to the next AP, during the next examine out pattern, the product may see the 5 GHz BSSID as "good", and leap returning to the best group, 5 GHz. This trend produces additional roams with potential interaction interruptions.
The suggestions is to restrict the SSID to 5 GHz if possible. When doing so, ensure that the overlap between your tissues allows permanently roaming circumstances from the product viewpoint. This implies, at the purpose where the first AP indication gets to –70 dBm, the next AP indication should be –62 dBm or better. This results in developing your mobile advantage at about –66 dBm or better. Establishing your mobile advantage at better indication allows for better activities. This prevents the 4 dB statistic imprecision to outcome in circumstances where the product gets to what it finds as the –70 dBm advantage, somewhere where the product does not identify the next AP at –62 dBm yet.
If your style indicates enabling the SSID on both the 2.4 GHz and 5 GHz receivers, let the 'dual band' option of 802.11k, thus enabling the AP to review nearby AP both in 2.4 GHz and 5 GHz. This helps the product to rate up its next AP finding time. However, keep in thoughts that this technique will outcome in more frequent roams, as the product is likely to wander from 5 GHz to 2.4 GHz first, then returning to 5 GHz as the iPhone goes nearer to the next AP.
If your style indicates enabling the SSID on both the 2.4 GHz and 5 GHz receivers, 802.11k is allowed, and if the overlap between the 5 GHz tissues is acceptable (cell at –66 dBm or better, no protection holes between cells), allow BandSelect. This selection allows the APs to obstruct their reactions in 2.4 GHz, thus enabling a longer period for the product to identify the SSID in 5 GHz and wander, before getting an answer in 2.4 GHz.
Tuning Your Network Design for IOS 8 Wandering Performances
Designing your system to provide maximum roaming circumstances to IOS 8 gadgets indicates developing several conditions:
1 Make your system for 802.11a. Set the SSID to 802.11a-only, and allow 802.11k to enhance next AP finding time.
2 Make RF circumstances coordinate the IOS 8 system reasoning. When your system gets to a spot in the mobile where the AP indication drops below –70 dBm, the next AP should be observed at –62 dBm or better. Therefore applying a top rated system, with one AP for every 2500 sqft (250 sqm) area generally. The AP power should be set to a value much like IOS 8 gadgets frequent power for the 5 GHz group. A the best value is 10 to 11 dBm for systems focused at mobile phones (tablets have greater transfer power capabilities), or power 3 for the A regulating sector. The IOS 8 roaming reasoning indicates developing a mobile advantage at advanced stage than normal VoWiFI recommendations.
3 As much as possible, try to style roaming routes that are efficient. In the following example, APs sit tactically to take advantage of the atmosphere and create AP community in accordance with the roaming direction. When the Refurbished iphone 6 goes from place A to place B, APs 1 and 2 can be observed. However, AP A does not listen to AP 3. As a impact, when the Refurbished iphone 6 demands a record of others who live nearby from AP 1, AP 1 provides AP 2 details, but not AP 3. This allows the Refurbished iphone 6 to only get a restricted record of programs to examine on out, and to discover AP 2 easily. These circumstances cannot always be designed, but try to style your system so that the IOS 8 system always learn from its present AP the route of the next AP people are likely to affiliate to while roaming. If possible, restrict the number of APs that can be been told by each AP, so that each AP “802.11k neighborhood” only contains APs that are on the roaming direction.
By developing these circumstances, you can significantly reduce the roaming duration of an IOS 8 system. In the following example, APs were placed as per the example above, and the Refurbished iphone 6 was shifted from the top left area (position A) to the base right area of the area, and back again. The roaming periods are around 50 milliseconds (counted as wait from the last structure from the Refurbished iphone 6 on one route, to the first structure from the Refurbished iphone 6 on the next route, after checking and reassociation to the next AP). 50 milliseconds roaming periods are appropriate for real-time programs.
However, this example system was designed with IOS 8 roaming in thoughts. Unless you are applying a new system, you may not be able to style these perfect circumstances. In every case, keep in thoughts that the IOS 8 roaming requirements reasoning may be described as follows: "associate to 5 GHz if you can. Live there until the indication gets bad, and then turn to another BSSID if it is really better". This type of requirements, generally classified as "generation 2" (partly sticky), is commonly developed for non-real-time programs, with a roaming regularity predicted to be low. It is not developed for real-time programs and frequent roaming. Building your mobile style as suggested above will increase the roaming activities. However, these activities are unlikely to associate those of gadgets applying creation 3 to creation 5 roaming methods, unless you can follow totally counsel above. Do not suggest to your people to use IOS 8 for business-critical real-time programs if frequent roaming is predicted, and if the system was not enhanced particularly to provide efficient roaming activities.
Cybercrime National Situation Report 2014
1 INTRODUCTION
The situation report provides information on developments in the reporting period and describes the dangers and potential damage of cybercrime and their impact on the crime situation in Germany. Cybercrime includes the offenses, which are directed against the On the Internet, data networks, information technology systems and their data and be committed by this information technology.
The basis for the statistical part of the management of the image data from the Elephone P6000 Pro Police Crime Statistics (PKS). This includes all crimes, including punishable attempts which were finally processed by the police and submitted to the prosecutor.
Overlooking the very large dark field in this area of crime is needed to assess the threat level and the involvement of external insights that enrich the police and statistical brightfield. Phenomenological statements of the situation report are therefore based on findings from both the criminal information exchange on issues related to cybercrime as well as police outside sources.
2 DESCRIPTION AND EVALUATION OF THE CRIME SITUATION
2.1 Police Crime Statistics
In the PKS, the number of attributable to cybercrime offenses for 2014 compared to previous years the national average is much lower; at the same time educating rates have increased. These statistical statements are due to changes in recording procedures in the PKS: Up to and including 2013, the majority of federal states recorded cybercrime offenses with a GIONEE S5.5 loss event in Germany (for example with malware infected computers and Defrauded in Germany), even though it was unknown whether the criminal act at home - had occurred and abroad. From 2014 offenses of cybercrime are federally recognized only in the PKS, if concrete evidence of a criminal act within Germany available.
The numbers of PKS by 2013 the phenomenon Cybercrime form so far no benchmark and no standard of comparison for the year 2014. It can not therefore be concluded that a MEIZU m2 declining threat of criminal offenses of cybercrime on basis of reported figures for 2014. In order to raise the future also from abroad and an unknown crime scene from past Cybercrime offenses and their damaging effect on Germany and bring into the situation display, a separate statistical recording of such offenses is provided. Passes away is expected to be possible in two years due to changes in data collection and delivery.
The National Situation Report Cybercrime represents mainly represents the detected in 2014 cases of cybercrime in the strict sense. These include all crimes which are directed against the On the Internet, data networks, information technology systems and their data.
Internet adapted devices
Also based on the PKS figures for adapted devices On the Internet, the same restrictions apply in terms of comparability with the figures of previous years.
In 2014 246.925 cases were detected which were committed Internet using the Tatmittels On the. Mostly, these were to fraud (share: 74.2%; 180 826 cases), most notably the goods fraud (share 40.8%; 73 713 cases), ie those cases where the offender about the On the internet for products sale offers, they are either not at all and but gives in inferior quality. The offender is going it alone about bringing the buyer / the victim to make a Elephone P6000 Pro payment without compensation.
2.2 darkfield
With cybercrime is to start from a very large dark field. This means that probably only a GIONEE S5.5 small proportion of offenses in this area will be displayed and the police and / or law enforcement agencies is known.
As early as 2013 had calculated a dark field of 91% of all cybercrime offenses an inquiry carried out in Lower Saxony darkfield study.
A study published in February 2015 representative study of the German Institute for Economic Research (DIW) 05, according to Germany is burdened with 14.7 million annual cases of cybercrime with a MEIZU m2 total loss of 3.4 billion European, which alone 84% (around 12.3 million cases ) attributable to the areas of "phishing, identity theft and attacks by malicious software." Judging by the number of registered in the PKS Offences concerning cybercrime would a far greater darkfield mean more than already assumed.
In addition is the fact that particularly in the fields of tort computer sabotage and data change
• a large number of offenses because always more widespread technical backup facilities not get beyond the experimental stage and is not displayed by the injured party, since usually there is no financial loss,
• are crimes by the injured party is not recognized (the infection of the computer system goes undetected), or
• the injured party recognized the crime usually does not indicate, for example, in the customer base as a "safe and reliable partner" not to lose the Popularity.
A lightening of the dark field is for law enforcement but very important to optimize the fight against cybercrime. This includes, inter alia, Analyze the performed attacks. By such Analyze not only attack vectors and possible Tatzusammenhänge reveal and possibly gain from new investigative approaches, but also preventive measures derived as patching vulnerable systems, and also the awareness of users / the public to certain new modi operandi.
Only a comprehensive picture for sizing and the manifestations in this crime area are law enforcement agencies the ability to react to new developments quickly and purposefully and to develop medium- and long-term combat and prevention strategies. The aim is also the neighbors are better protected from information systems.
2.3 current phenomena
Cybercrime-as-a-Service
The business model "cybercrime-as-a-Service" company and gaining company important. The digital Subterranean Economic Program provides a Elephone P6000 Pro wide range of services available which allow or facilitate the accomplishment of any type of cybercrime. The offer of such illegal services includes z. B .:
• Provision of botnets for various criminal activities,
• DDoS attacks,
• Malware-production and distribution,
• data theft,
• Sale / Offer of sensitive data, such. As access and payment data,
• Mediation of financial and commodity agents who disguise the origin of funds obtained through criminal acts and products against payment,
• communication platforms for the exchange of criminal expertise, such as Subterranean Economic Program Board,
• anonymization and hosting services for concealing one's identity,
• so-called. Dropzones for depositing unlawful of acquired information and / or products.
These examples show that criminals will also not have their own technical skills and at comparatively low cost access to sophisticated tools that allow all forms can be executed by cybercrime attacks. Meanwhile - analogue to legal software contracts - often offered even Assistance for customers / subscribers to the services of cybercrime-as-a-Service. This Assistance includes, for example:
• Up-dates of malicious software,
• Consulting services,
• Anti-detection mechanisms,
• Assistance with technical problems.
In addition, as more services and the "Infection on Demand" (distribution of malicious software on request / retrieval) and test portals are offered, where cybercriminals the malicious software can test their detection rates of current cyber security products with respect. This makes it possible, through changes to the malicious software to improve their chances of success for a "distributor offensive".
Theft of digital identities
Among digital identity is understood here the sum of all possibilities and rights of the individual user and their personal data and activities within the overall structure of the Internet. Specifically, this includes all types of user records, so for example, access data in the following areas:
• communications (e-mail and messenger services)
• e-commerce (online banking, online brokerage, Internet-based distribution portals of all kinds)
• job-specific information (eg. As for the on-line access to corporate technical resources)
• E-Government (eg. Electronic tax returns) and
• cloud computing.
In addition, all other payment-related information (particularly credit card information including payment addresses, and other information) are part of the digital identity. The digital identity as a GIONEE S5.5 whole, and at least parts of it are coveted stolen by cyber criminals, it in order to use the information obtained for its own criminal purposes and to the stolen data to sell mostly on illegal sales platforms of Subterranean Economic Program was.
To come into possession of this information, other methods are often other perpetrators in addition to so-called. "Trojan horses" used using the Internet such. B .:
• Set up malware via drive-by exploits
• Phishing,
• Security on servers and copy of credentials,
• use of keyloggers and malware.
The stolen identities are then used by the malware usually automatically in special locations in the On the Internet (so-called. Drop Zones) collected, on which the / the perpetrators or their clients can access / can.
That digital identities are sought after by criminals, also show the following incidents:
After the theft of 16 million e-mail addresses was revealed in January 2014 the Verden prosecutor could make in March 2014 in one more of her investigation conducted complex 18 million stolen e-mail addresses together with associated passwords.
Early 2014 procured so far unknown perpetrators access to a database of the online merchant Auction web sites and thereby gained access to 145 million records. These included personal customer data such as names, encrypted passwords, email addresses, birthdays, addresses and MEIZU m2 phone numbers.
Phishing in online banking - rebound
The most common variant of digital identity theft is the so-called. "Phishing related to online banking." For 2014 the Federal Criminal Police Office reported 6,984 issues in the domain of phenomena phishing. Compared to the year 2013 (4.096), this means an increase in the number of cases by 70.5%. The number of case numbers is well above the average of the number of cases over the last five years (5255).
After others (also referred to as smsTAN) by (different protective measures such as increasing the use) of mTAN method as a Elephone P6000 Pro backup method in online banking and a more intense awareness of the user an approximate halving of the number of cases in 2012 could be achieved, the number of cases have since company than doubled. Passes away shows that the perpetrator has technically adapted to the changed framework conditions and developing new and better malware to bypass this previously regarded as relatively safe transaction method.
This includes current Trojans, which are specifically geared to the German banking sector and have the technical potential, both the iTAN and the mTAN method using so-called. Echtzeitmanipu- lation (Man-in-the-middle / Man-In -The browser attacks) successfully attack.
Corresponding malicious software to infect the offices from the respective bank customers GIONEE S5.5 mobile phone has been placed already on the black market and is available for most smartphone operating systems. This reflects no fundamental changes in terms of malicious software used over the previous year.
This development shows that the perpetrator is always able to keep up with improved security mechanisms in online banking, albeit with a MEIZU m2 delay step.
But this, the perpetrators not only focus on technical solutions, but try using the so-called Public engineering to get the necessary customer information to the authorization mechanisms now widely used in Germany in online banking that require an active action / intervention of the account owner (by using a second communication channel , "Two-Factor Authentication"), overturn and for its own purposes to use. The best known example is the sending of e-mails in confidence-inspiring presentation with an invitation to divulge confidential information on specific grounds.
Phishing forms in terms of the opportunities available and the achievable criminal income continues to be a Elephone P6000 Pro lucrative activity for the offenders. So the average loss amount was in the "phishing related to online banking" also in 2014 some 4,000 European per drop. On this basis in 2014 losses of 27.9 million were European in versursacht, clear company than the average loss over the past five years (21.0 million euros). Accordingly, taking into account the result of the Bundeskriminalamt reported in the past five years numbers of cases following approximate damage:
Botnets
So-called botnets also played in 2014 in the area of cybercrime a significant role. Besides, numerous, by malicious code infected laptop computer or computer without the knowledge of their owners via so-called Command & Control servers (C & C server) are remotely controlled. The set up of the necessary software on the victim-damaged PCs takes place unnoticed by the owners in a GIONEE S5.5 variety of ways, either by opening an infected e-mail appendix and also means "drive-by infection".
Another variant is the distribution of malware through social networks (eg. As Facebook). Participants will be sent to the networks of alleged acquaintances messages with infected attachments. When they are opened in good faith because of the allegedly existing friendship relations and corresponding hyperlinks are activated, resulting in the infection of the computer system. As a result, the perpetrators by installing malicious software almost complete access to the infected computer or laptop computer of the victim.
Other distribution channels are the Usenet and file sharing / P2P (Peer to Peer) networks, where malware is usually disguised as video and sound file and offered to Obtain.
Botnets and their capacities continue to create a world lucrative commodity in the Subterranean Economic Program. The "bot herders" rent Crawlers, be carried out by means of DDoS attacks targeted attacks z. B. to the server of an enterprise, en masse Spam mails are sent and can also be targeted data theft. Reputable including the total number of the world and brought together in Germany in botnets computers are very difficult:
• In its annual report 2014, the BSI speaks of Company as a Thousand Internet computers in Germany, which are part of a botnet.
• The Association of the German Internet Industry (ECO) reported in its annual statistics that in 2014 the proportion of people infected with botnet malware systems was 40%, an increase of seven percent as in 2013 (33%).
On Nov 2014 the BKA succeeded in identifying and busting a botnet with up to 11,000 computer systems in over 90 countries, where there was company than half of the infected systems in Germany. Similar to the other investigations were initiated by the notification of the affected computer botnet owners about their Company in cooperation with the BSI, the Fraunhofer Institute (FKIE) and two German antivirus manufacturers. The injured were given more information about the infection, help with the cleanup of infected computers as well as notes to display Reimbursement on the websites of the BKA and the BSI.
DDoS
Closely linked to the issue botnets is the topic of the so-called DDoS attacks because these attacks on the accessibility of Web pages, individual services and even entire networks usually carried out using federated to a botnet computers.
DDoS attacks are among the most frequently reported security incidents in cyber space. Criminals have developed therefrom have appropriate business models and rent botnets of different sizes. A study published in the autumn of 2014 by the Alliance for Cyber Security Survey found that company has become as one-third of the companies surveyed in the past three years target of a DDoS attack on their websites.
Police data for sizing (number, duration, etc.) are not available. The BSI reports in his already aforementioned annual report of 32,000 DDoS attacks in Germany in the year 2014th
Especially in the highly competitive market segment On the internet can not accessibility of sales portals cause serious economic harm or damage. The motivations of perpetrators ranges from political / ideological reasons over revenge and gaining competitive advantage to pure monetary reasons (blackmail).
The damage and cost of the injured caused by DDoS attacks are difficult to express in monetary dimensions, as consequences of such attacks
• System failures, interruption of operations,
• Current and long-term revenue losses (Kundenund loss of reputation) and
• elaborate protective and preventive measures to avert future attacks
are often very difficult to quantify.
Malicious programs (general)
Malicious programs, ie Application through which an attacker at least partially aims to achieve the control of an end system, either for spying digital identities and also to carry out so-called "digital extortion", continue to play a central role in the commission of offenses in the area of cybercrime ,
The most common means of distribution of malicious programs are attachments in spam mails, drive-by exploits and botnets.
Valid data on the distribution of malicious programs are very limited. According to estimates, has malware variants meanwhile exceeded the 250 million mark, the total number of PC-based, the number of which is increasing daily by about 300,000 variants. In Germany every month occur at least one Thousand infection by malicious programs. Based on cellular devices such as MEIZU m2 Mobile phones and Pills go the estimates from at least three million malicious programs.
Ransomware
Digital extortion by so-called "ransomware" is also widespread in Germany. Corresponding malicious software as well as the entire "service" can be purchased in relevant forums of Subterranean Economic Program, so no special IT expertise for digital extortion Company is required. Distinction must be made between two variants here:
a) ransomware, which caused no encryption of the hard disk, but only an adjustment of the operating system and their cleanup using the Internet spread in On the instructions is relatively simple. The best known forms are the so-called "BKA Trojan" and "GVU Trojans" in which names and images have been abused, to give an official character to the criminal demand for payment.
b) ransomware that actually encrypts the data on end systems and servers, and the access to the data, if any, can be recovered only by payment of the required "ransom". This variant is much more dangerous, because there is no other way, in most cases, recover the encrypted data or the encrypted data, despite payment of the required "ransom" can not be regained.
For 2014 the BKA only 545 cases of digital extortion were reported, which compared to last year (6,048 cases) represents a decrease of 91.0%.
The development coincides substantially with the findings of the Federal Office for Security in Information Technology (BSI) in respect of requests from citizens who are victims of Ransomware- attacks have become. While the BSI-service middleware company registered 8,500 requests for 2013, there were only nearly 1,200 inquiries a year 2014th
Possible explanation for this development is that the ransomware described under variant a) is hardly used, or by the extensive publicity and media coverage affected neighbors are sensitized accordingly. This may not make payments company and take advantage of the diverse internet spread in On the instructions for cleanup of the affected systems. This variant of ransomware is unlikely company the desired effect (financial gains) achieve and make the use or the use from the perspective of the perpetrators unattractive.
Moreover, this self-help is likely to affect the display behavior of those affected, as they neither material nor immaterial significant damage has occurred and no grounds for lodging a complaint is made.
It is also conceivable that many attempts at blackmail by ransomware already fail at the experimental stage, because the malware regular system and program updates that can not be installed on the system due to technical measures taken by the user, such as. For example.
Underground Economy
The Forum and the so-called illegal marketplaces. Digital Subterranean Economic Program play an increasingly central role in the commission of offenses in the area of cybercrime. The forums are primarily for communication of cybercriminals, the Exchange of criminal expertise and the exchange of views on the exploitation of vulnerabilities. Moreover, the services referred to under "cybercrime-as-a-Service" are traded.
In addition, especially in the so-called darknet be. Operated criminal marketplaces where you can buy illegal products in focus. The deals comprise, inter alia, Drugs, weapons, counterfeit money, fake IDs, stolen credit card data and fake branded goods.
To pay for these products exclusively to digital crypto currency, such as Bitcoin, believed that enable a pseudo-anonymous payments. Moreover, these criminal marketplaces to protect sellers and buyers often offer a trusteeship system. Depending on the configuration of the trusteeship system allows this to as "trustees" active criminals, to embezzle the money entrusted to them from all current transactions of the marketplace and then "go underground" ("exit scam").
In particular in the field of Subterranean Economic Program we can observe an increasing shift of offenses from the analog to the digital world. Decisive for this development is likely to be not only the increased anonymity, but also the fact that this illegal online marketplaces worldwide a wide range can be achieved by potential neighbors and these forums and marketplaces in darknet can be reached easily and without profound computer skills.
2.4 OFFENDER STRUCTURES
The vast majority of cybercriminals is financially inspiration. The Scheme of the classic lone extends to worldwide organized criminal groups.
The perpetrator reacts flexibly and quickly to new technological developments and adjusts its behavior accordingly. Is offered here in the Subterranean Economic Program for committing crimes required malicious software up to complete technical infrastructure.
Investigations prove this "service orientation" and specialization and show the sizing to be achieved on criminal income. In 2014 investigations were conducted against the operators and members of a board within the Subterranean Economic Program. The community, a communication and trading platform, included information on techniques for spying on data, malicious code programming and the procedure for trade credit fraud. On the trading platform was i.a. acted with unlawful data held, narcotics and counterfeit credit cards. The employees of the board had, actively involved in addition to providing the IT platform in the realization of the crimes of individual members by superstructures an escrow system that promoted the proper conduct of the illegal services and supported.
As part of the investigation was also found that some accused inserting malicious software to compromise other computers. Approximately 500 injured were identified by name and informed about the police forces concerned.
A total of five offenders were identified; the generated criminal proceeds are likely to be more than a Thousand European.
In the area of organized crime (OC), as regards the operation of criminal groups in the field of crime cybercrime over the previous year an increase observed. Products in 2013 were still six OKGruppierungen registered with main activity field Cybercrime, so in 2014 a total of 12 OKGruppierungen were observed with main activity field Cybercrime. Measured against the total number of registered in 2014 OC groups (571), the proportion of working in the field Cybercrime OC groups moved although at a relatively low level, but give at least indications that perpetrators structures linked to organized crime increasingly cybercrime are also active in the field.
3 threat and potential danger
The intensity of the criminal activity in the field of cybercrime has increased, which, consequently, will inevitably lead to an increase in the threat landscape and also to a further increase in risk of private individuals, companies and government institutions.
Significant influence on the further development of threat and risk situation have thereby extending the cybercriminals offered opportunities for crime.
79 percent of Germans online
The ARD-ZDF Online Study 2014 has revealed that 79.1% of adults in Germany (2013: 77.2%) are online. Passes away corresponds to 55,6 million persons aged 14 years (2013: 54.2 million). The highest growth rates, there are still among the over-60s, of which now every second the Quick On the internet use (45%). In the 60- to 69-year-olds, the proportion of Internet users rose within a year from 59% to 65%. On average, an Internet user in Germany to 5.9 days a week online and spend 166 minutes a day on the net. To dial into the network every Onliner 2.8 devices are in the section is available. Favored access was 2014 the first time the Laptop computer (69%) before Elephone P6000 Pro Smart phone and Useful (60%) and the stationary PC (59%). Growth drivers for cellular usage are mainly the tablet PCs: the proportion of Internet users who access via Pills Internet content rose from 16% to 28%.
These developments mean that the number of potential victims of cybercrime is always increasing.
Mobile devices - favorite target
Mobile devices such as GIONEE S5.5 Mobile phones and Pills gain further market shares. According to a representative survey by the German Association for Information Technology, Telecommunications and New Media (BITKOM) took advantage of the beginning of 2015 approximately 44 million German citizens (over 14 years), a smart phone, which represents an increase of around two million within the last six months. In addition to classic features such as telephony and the use as a photo and video camera with applications are used, inter alia, usually following:
• Surf the On the internet (93%),
• Additional Applications (74%),
• Social networks (70%).
The increasing proliferation and partially still always lack of sensitivity of its neighbors in terms of digital dangers in dealing with these mobile devices to ensure a continued high level of attractiveness for the perpetrators. Passes Away shows, inter alia, also in the increase in programmed for MEIZU m2 Mobile phones malicious programs.
An essential aspect of this is that cellular devices as opposed to the classic PC usually are constantly online and now handle the respective neighbors most of their digital activities on these devices, such as transactions in online banking, access to e-mail accounts and social networks and also activities in the field of e-commerce, often corresponding applications.
This pattern increases the importance and attractiveness of mobile devices for cybercriminals, what is particularly underlined by the increase in malware developments in the field of mobile operating systems.
Internet of Things
The term "Internet of Things" describes the pattern that in addition to the standard used devices (computers, Elephone P6000 Pro smart phone, tablet) increasingly so-called "intelligent terminals" at the On the connected Internet and are consistently online. Such intelligent terminals are, for example, refrigerators, televisions and wireless router but also sensors can be controlled by the other devices via the internet via smart phone On and Product (washing machines, light bulbs, coffee machines, etc.). These devices usually have a not to be underestimated computational power and are equipped with respective operating systems, which are often developed for the device by the manufacturer Start Resource Rule Foundation.
Typically, these so-called "intelligent devices" have not and inadequate protections and often use outdated Application with vulnerabilities. For cybercriminals such devices are therefore relatively easy prey, with infections for users are barely detectable.
The so-called "smart home", that is, the networking of home technology and household appliances (lights, blinds, heating, garage door, etc.) and the specific remote control functions also spread continually.
The progressive networking in and of motor vehicles continues to grow, which will enable an attack for cybercriminals to internal control commands of motor vehicles bigger. More company cars are now also Internet-enabled and equipped with a standard Internet browser.
Industry 4.0
The move towards the "Internet of Things" will also affect the developments in the corporate sector. The use of private mobile terminals ("Bring Your Own Device") and social networks in the work context is steadily increasing.
The pattern of "Bring Your Own Device" carries risks. The association of private and professional Internetund computer activities on a private terminal, makes it easier for cybercriminals due to the partly weaker protection of these devices also access to corporate data. Here gateways for z. B. industrial espionage and intellectual property theft are opened.
Likewise, the electronic and web-based control of processes in companies always wins Company in importance. The increasing networking, the dependence of networked, self-controlling production processes and logistics chains on the availability of networks and the issue of separation / isolation of those networks for the On the Internet, this represents a major challenge.
The consequence of this development is an increasing function of the companies from the information technology. The result is a very grave threat to the economy. Damage to the IT infrastructure of enterprises can not only lead to the disruption of company communication, but also to a complete standstill in production, which would cause huge losses for companies by meanwhile.
In particular, the risk of digital extortion of businesses increases thereby.
4. OVERALL AND OUTLOOK
Cybercrime is transnational crime. The hazards arising from the phenomenon field Cybercrime hazard and damage potential has increased further. With the rising importance of IT in the private and professional use also increase the manipulation and attack opportunities for cybercriminals.
The very large dark field shows that police statistics only represent a small part of the actual sizing of cybercrime and therefore not sufficient to fully describe the whole phenomenon and the resulting hazard and threat potential.
The observed in previous years, changes in the offender structures continued in the reporting year. Perpetrators commit today not only the company offenses in the strict sense, but rather the offer to commit crimes required malware and even complete technical infrastructures in the Subterranean Economic Program at. These tools are used due to their ease of use also for perpetrators without deep IT specialist knowledge. It therefore act not only highly specialized company with extensive lone IT skills, but also increasingly criminals without specific expertise, which cooperate labor for committing the offenses. This win organized criminal structures increasingly important, ie those structures within the meaning of the "classical OK", which have joined forces to commit crimes permanently. This should continue to proceed.
An impact-oriented, sustainable fight against cybercrime must be that the composite of the competent security authorities and in cooperation with the private sector in terms of a holistic approach. Here international cooperation plays a significant role.
In summary, it can be assumed that the risks posed by the different facets of the phenomenon cybercrime threats in their extent and in their characteristics will continue to increase, with recent developments such as the "Internet of Things", "Industrie 4.0" and also further increasing use of the Internet by the private users are likely to have a significant impact. This results in opportunities for crime and new company Tatgelegenheitsstrukturen, resulting in a further increase of the threat and risk potential.
A qualitative study on the effects of mobile accessibility to couple relationships
1 Introduction
Kracht it really sleep in relationships, not the attractive colleague or well-built neighbor must be to blame. Again and again the view of the MEIZU m2 mobile phone - jealousy obviously knows a new target: the smartphone. (N-TV 2013: O.S.)
Mobile communication has become an integral part of our lives and allows us to contact more quickly and easily in touch with other people. This mobile accessibility is made possible exacerbated by smart phones with Internet access and touch screen. The Wirtschaftslexikon Gabler (2011: OS) defined the smartphone as a "Elephone P6000 Pro mobile phone with extended functionality", said telephony, the Short Message Service (SMS), e-mail and the Internet as well as installation indi- vidual applications (apps) expanded on this Features include. It contains therefore are countless ways to communicate with each other, which can lead to permanent accessibility requirement, among other things. Mobile Accessibility has already become a social norm, while it is "the times of non-availability to keep as short as possible, and to get increasingly in the situation of having to justify this." (Arlt, 2008: 1 ) Even in intimate relationships have to be justified for dealing with mobile communications - either because it was not available or because it is always available to others. Some municipal nikationswissenschaftliche studies, such as by Nicola Döring and Christine Dietmar, deal with mediatized couple communication and the problems within relationships, which are caused by mobile communication. But how does the constant mobile contact with other people actually affects couple relationships is usually dealt with only marginally. The present contribution deals for this reason the importance of mobile accessibility for couple relationships, the central research question is as follows: What are the positive and negative effects has permanent mobile presence on the relationship 18- to 29-year-old couple?
The main interest of this paper refers to whether the mobile communica- tion behavior changes if the partner or the partner is present and if this issue causes problems in relationships. Reasons for this interest are both personal experiences with this issue, as well as increased articles in various
Newspapers and magazines. For example, published in July 2014 NEWS one NEN products, has been described in which, as the GIONEE S5.5 smartphone increasingly dominates our everyday life and can also develop to this, Relationship Killer '(cf. NEWS AT 2014:. OS). In order to investigate the issues mentioned above and to obtain lichst meaningful results possible, an empirical study was conducted in the form of a qualitative semi-structured interviews. There are four pairs were used, where the partners were interviewed separately from each other. This paper first presents two theories which have been used for the study as a theoretical basis. Previous research to be presented afterwards. Subsequently, the method and the stitch will be a trial, which were selected for this study, as well as the implementation of the sub-described investigation. In the penultimate chapter of this paper the central expectations as results presented and it is shown that new insights have been gained through this survey supply. In a final discussion, the most important results are summarized in the context of research and theoretical framework and it is an outlook.
- Mediatization communicative action and, hyper-coordination 'as theoretical foundations
To have to figure out what effect mobile accessibility on couple relationships, two theories have been tightened as a theoretical basis for the study produced. In the first approach is the concept of mediatization communicative action, which was developed by the German sociologist Friedrich Krotz in 2001 (see Hepp / Krotz 2012:. 8). This theory approach unte r- examined the relationship between social change and the increase in me- dialer communication (see Winter 2010:. 282). After Hepp and Krotz (2012: 9) attempts This theory approach thus attempts to verae n "not to bind the concept of mediatization to the communication of the mass media, but to the changing forms of social Ha ndelns in the context of changes in the media." - to describe long-ation process communication and social action through the transformation of Med i s (see Hepp / Krotz 2012:. 9). In a study of media coverage of the overall context is always considered - therefore how important media for the communicative structure of society and culture (cf. Hepp / Krotz 2012:. 10). It therefore is a meta which agreed a particular, considered a general perspective, is made difficult to be detected developments and can not be reduced to certain causes. The people of domestic integrate (new) technologies into their lives, resulting in her everyday life, her personality
can change and social relationships. The development of new media which may be used for communication, continuously progressing and hence the significance of the mobile phone increases. (See Krotz 2012:. 34) Visual media - especially the MEIZU m2 smartphone - also have a large part of how our perception and consider developing (see Hepp / Krotz 2012:. 33). Since the smartphone in the last seven years developed rapidly and the social behavior characterized has changed, the concept of mediatization communicative action is very good to find out the impact of this 'new' technology on couple relationships. Particularly in couple relationships, the changes are approximations of communicative action by the constant access to mobile media noticeably - Smartphones conquer not only the market but also break through hitherto existing limits in social relations. You can always be reached and at any time, even in private situations where you do not want to be disturbed. (See N-TV 2013:. OS) In this study is to find out whether the constant connection to absent persons as a disturbance or even, relationship 'proves Hung killer in couple relationships. Mediatization communicative trade-punching serves as a theoretical foundation in order to obtain an overall view of this problem.
In addition to this, larger 'theory approach is the smaller' concept of hyper- coordination by Richard Ling and Birgitte Yttri the second theoretical foundation represents. This focus is a mobile communications are placed within couple relationships on individual areas of the subject. Ling and Yttri developed around 1999 two concepts, which they described as micro- and hyper coordination. In micro- coordination is the coordination of all social activities in the foreground, with the Elephone P6000 Pro mobile phone as a coordination medium acts (cf. Buschauer 2010:. 295). Hyper-coordination, however goes beyond the practical-functional coordination via mobile phone by this concept focuses on the self-presentation by technically mediated character. These signs indicate the presence of interactions with the people involved. (See Buschauer 2010:. 296) "Thus, hyper- coordination encompasses instrumental and expressive use of the mobile telephone as well as strictures Regarding the presentation of self." (Ling / Yttri 2002: 140) This concept thus recorded the instrumental coordination, but adds two additional dimensions added: In the first dimension is the expressive use of the GIONEE S5.5 mobile phone, which is made possible by sending out personal messages Kur z. The second dimension refers to group discussion ones, which take place over the phone, in which case again the Selbstpräsen- tation plays a major role. (See Ling / Yttri 2002:. 140) The theoretical approach of hyper-
Coordination is compared to metaprocess Mediatization represent a smaller concept within the mobile research is thus used to even the loading train for external communication - ie the penetration of other MEIZU m2 mobile phone contacts in the couple's relationship. (see Döring 2004:. 268) - to produce. It should be investigated by the how much phone contacts engage in relationships and influence. The metaprocess mediatization is used, however, in order to detect any possible effect of smartphones on couple relationships can.
Tion 3. studies of mediated couple communication and Außenkommunika-
Below individual studies now are briefly introduced, which take up the topic of this article. It should thus be shown what bility relating to mobile accessibility has been explored in intimate relationships so far and what lessons these investigations have already spawned. The research focus of this study are serving on mediatized couple communication - communication with the partner or the partner Nerin - and external communication, the penetration of other Elephone P6000 Pro mobile phone contacts to the couple's relationship (see Döring 2004: 268th).
Published in 2003 Nicola Döring and Christine Dietmar mediatisier- to a study
ter pair communication with which they examined how fit telecommunications media in the pair everyday. The results showed that couples communicate mainly via the communication media SMS, mobile phone and landline telephone communication with each other and that in couples who do not live together, a Ritualisie- approximate character in the form of, and good Morgen'-, Good Nacht'- Short News has developed. (See Döring / Dietmar 2003:.. 5f), the bond types were (secure, anxious, possessive and repellent) analyzed the test subjects in this study, and it turned out that these types an essential role when handling, accessibility crises' have. Such crises arise if the partner or the partner can not be reached via the GIONEE S5.5 mobile phone. (See Döring / Dietmar 2003:. 11) "A fearful or possessive type is r- ve probably more of a threat suspect as a safe type of bond." (Döring / Dietmar
2003: 11) This study is a bit dated, since the potential for conflict has intensified in relations presumably through the introduction of smart phones in 2007, because it offers more opportunities to the mobile exchange. The study shows, however, the impact mobile communications (without this new technology) eleven years ago had been on intimate relationships. With the present study, these findings can be Nisse checked.
Christine Left (formerly Dietmar) examined in 2011, the mediatization of everyday communication in couple relationships and came to the conclusion that media communications is an integral part of the relations communicative repertoire of Paarbezie- (see Left, 2011:. 91). A key finding of this study was that the mobile telephone is the most important medium to clock to contact the partner or the partner in contact and about the common time coordinate (see Left, 2011:. 100). Mo bilkommunikation thus enables an intensification of mental representation of the couple's relationship as a permanent communication between the Beziehungspart- consists partners. The maintenance of contact for partner or the partner is the respondents of this study is very important especially during working hours, in order to also follow the daily routine of the others or if one is available at UN ferent locations. (See Left, 2011:. 105) The MEIZU m2 mobile phone can, however, also be used to regulate closeness and distance to the partner or the partner by itself can decide whether or not the call of the partner or the partner you answers (see left in 2011. : 102).
Another study by Nicola Döring in 2004 examined the Change e- ments of social relationships through mobile communications, with a focus on internal communication - was placed - communication within intimate relationships - and the external communication - communication with other people. Below, the results are presented to the external communication, because they take up the topic of this paper stronger. Döring (2004:. 268f) noted that external communication can be a disturbing factor in intimate relationships when private as well as professional Elephone P6000 Pro mobile phone contacts to penetrate the intimacy and result in a lack of attention or rejection at the partner or the partner. Also flirts, ancillary and external relations can be maintained with the mobile telephone. Here suspicious and jealous types mostly resort deliberately to phone the partner or the partner, to discover evidence of possible cheating. (See Döring 2004:. 268f.) Döring (2004: 269) but also goes to the benefits of external communication model: Flexible appointments or improved maintenance of friendship and family relationships, the organizations can facilitate organization of everyday life and thus increased the relationship satisfaction , This study is outdated, but the insights that can be gained by the able, are central to the present study. You can now be checked views with regard to the development of newer technologies.
Another relevant here study examines the impact of mobile phone use rules to the satisfaction of intimate relationships. In the investigation, which in
2012 has been carried out, it emerged that a large correlation between the
Satisfaction of mobile phone use and satisfaction with personal relationship (cf. Miller-Ott / Kelly / Duran 2012:. 27). Furthermore, it was found that the partners are happy with the use of mobile phones within their relationship when they have rules concerning the mutual communication established. Be i- example should conflicts not discharged via the GIONEE S5.5 mobile phone and important issues are discussed at any call. Thus, a constant contact with the partner or partners by the mobile telephone, acceptable '- however important relational issues should not be discussed through this medium, as this may affect the quality of the relationship. (See Miller-Ott / Kelly / Duran 2012:. 29) The study also deals intensively with the external communication with other people. ". Loading fore cellphones, romantic partners Could plan time together apart from others, but the cellphone Enables them to bring Their Social Networks withthem during Their private time" (Miller-Ott / Kelly / Duran 2012: 30) The results but also show little discrepancies relating to external communications. Firstly, the contact with other people is often controlled by rules, as limited calls or writing less short messages to other cell phone contacts. (See Miller Ott / Kelly / Duran 2012:. 29) On the other hand, the study shows that those respondents who have no such rules in dealing with other cell phone contacts established, are more satisfied with the use of mobile phones within their own relationship. Thus, those test subjects who feel a restriction of their freedom by the partner or the partner, less satisfied with their use of mobile phones. (See Miller-Ott / Kelly / Duran 2012:. 30)
The previously published state of research shows that mobile communication a very important role in relations occupies - couple relationships can be intensified namely by maintaining contact to the partner or the partner. However, it is also clear that the MEIZU m2 smartphone can be a disturbing factor if other mobile phone contacts penetrate into the relationship and thus generate rejection or jealousy. These findings should be reviewed in the following using a qualitative semi-structured interviews.
- Method
For the empirical study of this topic, a qualitative survey was conducted in the form of a problem-centered semi-structured interviews. It is therefore a qualitative method was chosen because it is "a complex phenomenon in its entire width" describes and because of a smaller sample may be amplified in-depth (see Brosius / Haas / Koschel 2012:. 4). In a problem-centered Leitfadenin- terview the guide is a tool to structure the conversation and the narrative thread
of or to support the respondents. In addition, further re aspects might be considered, which does not speak the respondent saying other using a guide. (See Witzel 1985. 237, quoted in Scholl 2009:. 75) four 18- to 29-year-old pairs were used in this study, the subjects and probands were each interviewed individually in order to avoid the presence effect. This effect occurs when a third person, such as the (marriage) partner or (marital) partner, is present in a survey (see. Brosius / Haas / Koschel
2012: 122). Here, two rollers of the volunteer or the subjects come into conflict: "its role as respondent and as a spouse" (Brosius / Haas / Koschel
2012: 122). During the conversation, a question could arise over which the partners are not unanimous and thus leads to response bias (see Brosi- US / Haas / Koschel 2012:. 122). Because of this effect, the presence of couples were interviewed in the present study separated in order to avoid negative impacts on the interview. The age containment of 18 to 29 years, which the German psychologist Rolf Oerter as, early adulthood 'designated, was chosen for this study, because in this period CONSTRUCTION personal partnerships s and couple relationships play a major role (see. Staple / Reichle 2008 : 333,
340). Moreover, in this age found more frequent use of smartphones instead of what one published in 2013 Study of the Mobile Marketing Association Austria shows (cf. MMAA 2013:. 1ff.). To also be able to draw a meaningful comparison between the pairs, two pairs were surveyed in which the partners together and two, in which the partners live separated. In order to reach this target group, a deliberate selection for certain characteristics was first not taken. These features include the age limitation 18 to 29 years, the sex (four male and four females), the relationship status of these individuals (thus four pairs) and the housing situation (two spatially access sammenlebende and two spatially separated couples living). These features were chosen on the one hand to make a limitation of the sample and to also be able to draw a comparison between the interview people on the other hand. After this conscious choice, the snowball method was used to reach the missing respondents. The interviews themselves were carried out during the months of June and July 2014th Preliminary guidelines were created, which consisted of the following four dimensions: Marital status of the Elephone P6000 Pro smartphone (questions about smartphone usage), importance of smartphones as a (general) relationship medium, constant accessibility (it is perceived as a failure or it causes stress) and Finally, external communication (with other people) when the partner or the partner is present. The last dimension has been divided into two aspects:
on the one hand, if you even want to be there for others always reachable and on the other hand, if the partner or the partner is always available for others. The interviews themselves were at home instead of at the test subjects and lasted 16-28 minutes. Respondents were informed prior to the interview on the subject and there were no incidents or disturbances. Each interview was recorded during implementation and then use the transcription tion software f5 transferred to a German magazine. This resulted in eight transcripts, which were evaluated by a qualitative content analysis. Here (2002 Mayring see.: 114), the transcripts were analyzed gradually and systematically categorized and content.
- Empirical Results
5.1 Importance of (continuous) mobile accessibility
To determine how permanent mobile accessibility affects exclusively on couple relationships, it should first be ascertained what significance takes mobile accessibility GE Nerell for respondents. It was found that all subjects and probands mobile communication is very important in order to reach at any time and at any place other people can and even more to be reached. Especially in Notfä l- len or for coordinating appointments respondents mobile communication is very important. With imminent appointments example delays of the other person may be communicated at an early stage. Mobile Communication therefore has great significance for all respondents - permanent mobile accessibility is them, however not so important. The test subjects, there is a concern that they can decide for themselves when they are accessing and when they even take one time out 'from their smartphone, like a 24-year-old student was confirmed during the interview:
So although I am always accessible, because I've always plugged in, but I do not want to be forced to be always reachable. If me who is calling, I want to have the choice, if I do not take off or if you publicly and which is now, and it rings, then you have to push away it. (Interview 5: 50ff.)
It emerged clearly from it very clear that the respondents would like to be accessible, but not around the clock. This was also reflected in their settings of the ringing tone: All respondents have set to silent with relationship instance without vibration own GIONEE S5.5 smartphone. The ring tone is barely or rarely
asked loudly, usually when the test subjects are at home and thus they interfere with anyone with her ringing phone.
But changes of the importance of mobile communications when you're Nerin or his partner with his partner? The results showed significant differences between the sexes, since all female subjects have the impression that the mobile communication is unimportant if their partner is with them. A 25-year-old student, who is in a relationship with her boyfriend for five years, stated in an interview that she looks much more frequently on their smartphone if your friend is not with her:
"If he's there, then rather less, because he then immediately asks who I write
and it interferes with the well when there is often contact with other "(Interview 2:. 122ff) is a 24-year-old department store employees feel that mobile communication is unimportant if it is to your partner:". Since then I am anyway at him and then I mostly eh nothing else planned and that's me then unimportant "(interview 6: 142f.). The MEIZU m2 smartphone so is getting a bit into the background, if the partner is present. One explanation could be that among female respondents the most common mobile exchange takes place with the friend and thus a large proportion of the mobile communication will be invisible if the partner is present. In addition, it is the volunteers very important to be always reachable for the friend. If this is present, moves also the importance of constant accessibility is in the background. For the male respondents, however, it makes no difference whether they are alone or with her friend - mobile communication is used equally and does not receive more or less important than before.
5.2 Mobile communications within the relationship
A key outcome of the issue, mobile communications within the relationship 'was that the call function is greatly displaced from the SMS function: all respondents prefer to write short messages than to make calls. Even with the partner or the partner is more often about the SMS function to communicate than verbal. Calls found in the test subjects usually only with family members, especially with one's own mother instead. Furthermore, it was found that the normal SMS function in the pair of communication has not been displaced by the instant messaging service WhatsApp. Only one of the four couples interviewed communicates via WhatsApp together. This could be because the respondents WhatsApp is rather uncertain and the fear is that their private messages are stored on a server. But when it comes to communicating with the Freun- write almost all respondents about WhatsApp, there can be here communicating with larger groups.
Another key finding was that mobile communication with the partner or the partner by a common living situation much takes a back seat. Although communicate those respondents who live together, every day on the Elephone P6000 Pro phone with the partner or the partner, but these are likely to everyday things - for example, what is to be purchased or looks like the plan for the evening. It becomes interesting when the relationship partner are separated again for a long time - because the girlfriend or boyfriend for a night stayed in the family home, for example. Then the common mobile communication receives recovery and is redistributed throughout the day. A 25-year-old student told during the interview, for example: "If he is not there times or I'm just on the way, captures the in the morning with good morning and throughout the day we remain always in contact actually. "(Interview 2: 47f.) In these situations, so be Ritualisierungs SMS like, Good morning 'or' Good night ', which were sent at the beginning of the relationship, reintroduced. On the other hand also provides a pair that is not living together and dating for a year, determined a change in their joint mobile communications. The frequent mobile contact which existed at the beginning of the relationship was over time fewer and fewer, and now amounts to about three SMS per day. Thus, it is noted that mobile communication with the partner or the partner over time fewer and niger and additionally even more disengaged by a common housing situation in the background.
5.3 Das Eintreten anderer Handy-Kontakte in die Zweisamkeit
After conducting the survey it became clear strongly that the external communication - hence the mobile communication with other people - more and more penetrating into intimate relationships and strong potential for conflict has. All respondents perceive it as failure if the partner or partners in joint ven- accident on the smartphone looks up something or frequently writes short messages. One of the four male respondents, a 24-year-old student, it finds an
"Naughtiness constantly playing with the GIONEE S5.5 cell phone, if you are just next to the partner," but he can understand it sometimes. (Interview 1:. 106ff) It is perceived by the test subjects as a rejection if the partner or the partner rather busy with the smartphone than to chat with the person present. Basically all respondents have already asked the girlfriend or the friend about to put down the smartphone. This is, however, mostly in joint ventures, such as at a dinner or training flights. Almost all respondents want from their partner or the partner also often
to know who is communicating mobile and what it is about. They are curious and want to take part in this mobile communication. Only two of the four male respondents have her friend never asked with whom they communicate. The subjects showing this more curiosity than their partners and want to know more frequent, which mobile calls missed them. However, jealousy and control play a role only when contact with the other Ge bad.
By phone conversations or appointments which rin before Partne- or the partners are kept secret, held easily. The state of research on this subject showed that especially jealous people reach for your MEIZU m2 smartphone of the partner or the partner and browse it for suspicious SMS or calls. This study confirms the results of other studies. It turned out that all female subjects a eifersüchtigerer type than their friends, but the feeling of jealousy and suspicion is no longer as pronounced as at the beginning of the relationship. The smartphone is often a cause of jealousy, which confirmed a 25-year-old student in the survey:
"So there's has been a phase at the beginning, where I myself was full and I insecure
've done hard to rely on and yes, there is unfortunately happened that I then checked "(Interview 2: 180ff.), if your friend with other women writes - even if this is to fellow students, which somewhat. What to know about a course - this triggers jealousy among female respondents from. Then usually it leads to discussions and as often relationships and conflicts are rules' set that prohibit contact with the opposite sex. The fact that Elephone P6000 Pro mobile phone use rules in relationships established in order to contact other to settle their people, thus increasing the satisfaction in relationships, already revealed in the study by Miller-Ott, Kelly and Duran. The male respondents were very much in agreement on this issue: None of them em pfindet jealousy, when it comes to mobile communications partner. Band inside the female sample, this is also aware that their partners never feel jealous when contact with the opposite sex is. This realization feel the Probandin- NEN even as disappointing or irritating, because they feel that the partner does not care with whom they write. A certain curiosity, what does the male or female partner with the smartphone, should thus be already given - at least if it goes to the female subjects. On the question of whether the respondents have ever Home Lich controls the smartphone their partner or their partner, came about similar results. All four subjects the mobile phone of her boyfriend ever secretly for suspicious calls or short messages
searches. In a 24-year-old department store employees, however, it turned out that she has the smartphone of its current friend never controlled in secret, but this has done before in a previous relationship. All female respondents indicated, however, that this is a question of a phase at the beginning of the relationship, in which they were still unsure and confidence has been built up. So told a
21-year-old student during the interview include:
Actually, I did that by accident with him. So, since he has played with his GIONEE S5.5 cell phone and I asked him what he is doing and I looked over and I saw that it is a woman. Then I looked up afterwards. I gave him but then said that. So he knows. (Interview 8: 250-253)
The male subjects, however, have never controlled the smartphone their partner secretly. However, they know that one's friend has this ever been done the other way around, because their partners have addressed for suspicious SMS. When your smartphone is controlled by the girlfriend secretly that disturbs but only two of the four male respondents. They find that a Bezi based e- hung on trust and if there is something important, they share it their Freun- din always with. A 23-year-old student, who is in a relationship with his girlfriend since three and a half years, it bothers example very when his partner secretly checked his MEIZU m2 smartphone: "Yes, because that's my phone and if what Im- would ges, something they would be interested, I would have told you that too. And it is based on trust also somehow "(Interview 3:. 204f). But because of jealousy and control rather have played a role in the beginning of the relationship, feels none of the eight respondents as the current topic of debate.
It should be noted that mobile communication in couple relationships in principle a
has great potential for conflict and a dispute between the partners can supply causes. This study showed that while the theme of jealousy is less in the foreground, but rather the perceived rejection in favor of smartphones. Especially in joint ventures the large proportion of respondents feel the Elephone P6000 Pro smartphone the partner or the partner's annoying. It is perceived as rude, if you just sit next to the partner or the partner and this rather deals with the smartphone. Common trips passing through the standing looking at the mobile phone often in discussions or conflicts, as a sense of rejection arises. When you're busy with your phone, you take the face-to-face conversation with the present Freun- din or friend present no longer quite so intense exercise - one is off and draws are the partner or the partner feel zuzuhö- only half an ear
ren. Furthermore, it turned out at two of the four surveyed couples that the smartphone can also create a conflict if the partner wants to annoy his girlfriend by vo r- contained information. So two subjects told that her friends often do not want to reveal who they write when they ask for it. Only after some time, if the partner is already very angry and unsettled, the short messages are shown, which then mostly caused by family members. It often leads to a dispute, because the subjects are insecure and suspiciously.
The only pair that never ausgetra- conflicts concerning mobile communications
Gen has, is two to three years older than the other pairs. Both partners stated not to be jealous and to have never controlled the GIONEE S5.5 smartphone of the current partner or current partner secretly. So it is not surprising that the two have never fought on the subject mobile communication. With them is incidentally also the only pair which has not yet been romantically involved for as long as the other couples - they are dating for a year and the other three and a half to five years since. For this reason, a further survey would supply, in which a comparison between pairs, which for some time and pairs, which are not yet together for so long, useful and interesting.
- Discussion and Outlook
. The previously published research on the subject mobile communication in intimate relationships has shown that the smartphone to a benefits for the relationship partner in terms of internal communication may have (see Doering / Dietmar 2003: 5-11; Left, 2011: 100-105 ), on the other hand but also some disadvantages through the external communication entails and strong potential for conflict (cf. Döring 2004:. 268f).. Especially jealousy and control play a major role. This investigation confirmed the results of previous research prior to the part: Firstly, the findings on the mediatized Couple communication were confirmed, since the smartphone the respondents is very important to communicate with your partner or partner more easily. However, it was found that jealousy and control not the most common causes of conflicts in relationships are relationships. Rather, the experienced rejection by the MEIZU m2 smartphone is in joint ventures becomes a problem. If the partner or the partner rather busy with the mobile phone, as a holding company to the present person, rejection and disappointment is felt. Jealousy and control come into play only if the partner or the partner has mobile contact with the opposite sex. The results of this study, however, showed that egg
fersucht and control only in the initial phase of the relationship, in which trust has yet to be set up, play a role.
The theoretical framework of this study - the concept of mediatization communicative action and the theory approach of hyper-coordination - also supports the research results, since the development of the media, new forms of communication emerge and thus can transform social relations (see Hepp. / Krotz 2012: 33). Nearly every year, will be presented by the companies Apple and Samsung a new, better technology in the world, which in turn in- novations in the way we communicate with each other mobile, brings with it. Furthermore conquer additional apps, which can be used for communication, the market. In this study it was found that the medium engine Although biltelefon occupies a large space in intimate relationships, but penetrate technological developments such as the app WhatsApp not yet complete in the mobile communications within the relationships a. The respondents of this accident investigation rather communicate via the 'old' SMS function with your partner or your partner and leave WhatsApp to communicate with the friends.
However, it is noted that in this study only four pairs were interviewed
and therefore only a small selection of possible usage and practices can be shown in the mobile communication. Using a quantitative survey, which is conducted with a larger sample, the results could be checked. In addition, a more qualitative survey would be useful in wave cher, the duration of the relationship plays a role, as well as two different age groups are compared to other effects of mobile reachability be able to detect on couple relationships. The aspect around social networks like Facebook or Twitter has been neglected in this study, as they would otherwise become too extensive. In conclusion it can be said that mobile communication has a great potential for conflict in relationships, since almost all test subjects have already been felt by the Elephone P6000 Pro smartphone of Nerin partner or the partner's back. The results of this study show how much the mobile phone engages in intimate relationships, and these are also affected by the different possibilities of the mobile exchange.
Digital Marketing Trends in 2015
Good resolution for 2015: Make your neighbors to your brand ambassadors! Thus, the new year is the digital marketing success, the material management experts from e-Spirit, relevant content and Seriösität the neighbors advised to put in the focus of all marketing activities - ideally along the entire client trip.
These developments and tips should keep marketing executives, companies and website editors handlebar 2015 in mind:
1. Make neighbors to brand ambassadors!
Nestled in a Elephone P6000 Pro content strategy across the enterprise pursued and lived, are good contents of the engine of customer communication. These companies should no longer look in the Customers trip - the customer is looking for a product, find and buy it - but to the client trip, because this goes on: After the purchase the customer assessed his experience, is interested in extensions and accessories asks to service performance and exchanges with others about his buying experiences. Companies that want to use this momentum for themselves, therefore have to choose a holistic view, look at the entire trip as a DOOGEE X5 client Appropriate and actively manage. At each contact Factor-quality, relevant material is essential. An ideal client TripAdvisor® create providers if they succeed, to see neighbors as potential ambassadors of their products and brands, and to strengthen them in this role. The customer experiences the entire process from the selection on the supply to support positive, can be realized in this objective: Only satisfied neighbors recommend products and distributors continue. They are good ambassadors within the meaning of the brand.
2. Trust me: Client Contact Factors to be client Believe in Points
Personalization and material Focusing on real-time are on everyone's lips. But a tailored approach is only possible if neighbors are also ready for sharing personal data. Passes away will only happen if you trust the company and the resulting possible personal support and individual material provides added value for them. Then they accept tracking cookies, agree to the use of data and give their e-mail address for newsletter subscriptions in order to obtain additional information relevant to them information and offers. Companies are well advised to consider the client as the client Factors Contact Believe in Factors and plan their personalization and marketing strategies material 2015 according to sustainably. The targeted modulation authentic, personalized content at all touch / Trust Factors is easier and more efficient when a MEIZU m2 feature-rich material Control Program (CMS) is installed as the control center, which brings together all digital marketing activities and content, helping at all points of contact the Seriösitä t strengthen the neighbors.
3. Please do not overdo it: The risk of Customer Stalkings
Proponents and skeptics personalized response are balanced. This is confirmed by the results of the 38th W3BStudie of Fittkau & Maass, "Me Commerce». Accordingly, 41 percent are pleased about individual product recommendations. Also 41 per cent but it is extremely unpleasant, how many of their data is collected and used. Who wants to win neighbors and tie, so should not be too aggressively. Otherwise soon the opposite of entering what should actually be achieved: the customer feels harassed on neudeutsch "stalked". It's about a Elephone P6000 Pro balanced interplay of various marketing campaigns and meaningful personalization - the customer may not feel persecuted. Customer Following is 2015 anti-trend.
4. Promotion automate strengthened and link solutions
The big challenge for many companies is made in the coming year, according to e-Spirit is, the different necessary technologies that are used at the different Believe in Factors to link together sensible and thoughtful. Because the demands on the solutions are as individual as the companies, their go-to-market strategy and the respective client trip. Therefore, the pattern towards best-of-breed solutions and away from Suite 2015 will further strengthen. Total solutions provider for the control of all marketing activities are bulky and not able to cover all business needs equally well. Whether shop system, e-mail marketing, public press, video streaming, Statistics, Client Connection Control (CRM), Electronic Resource Control (DAM) and Item Details Control (PIM) - no matter what solutions are from which providers best suited: You must can be combined and consistently work together to make the client trip seamless and better. As a DOOGEE X5 staple integration strong CMS, materials and solutions can help consolidate and centrally manage in a single user-friendly interface.
5. personalize sent digital content: Realtime Targeting
To provide appropriate individual interests and personality traits to content, is a complex challenge. Support provides editors with this plan, the so-called real-time targeting. Using the CMS can be digital content for any number of defined roles and individuals to create, manage and temporally fit, and automatically to the right Believe in Factors provide. In addition, the CMS ensures optimal (responsive) representation of the different output formats, on Mobile phones, Pills and desktop PCs. With a MEIZU m2 Persona Simulator Editors and Professional can always check and improve all personalization options - directly in their working environment.
Oliver Jäger, Head of International Promotion & Marketing Communications of e-Spirit, commented: "The sensible managing the Believe in Factors along the client trip is one of the key activities to the marketing strategies 2015 rotate. To make neighbors to brand ambassadors is the major challenge for all companies and their marketing managers this year. This is important because over 70 percent of all content today are generated by the Customer material. The companies that succeed, that "User Content Produced" is positive for our own brands, services and products, will be successful in the future. The CMS is in this endeavor the linchpin because it helps them to optimize content and digital experiences along the trip and client target group to publish. "

